SINGLE PACKET AUTHORIZATION (PORT KNOCKING) EXAMPLE SIMULATION IN MININET
SPA is one method of port knocking used to dynamically modify firewall rules and allow access to specific port of a remote system. Details on this may be read from https://en.wikipedia.org/wiki/Port_knocking. We will be implementing a network with SPA authorization for SSH. Here the system is configured to allow access to SSH port (number 22) only after receiving an authorization packet from a remote system. The authorization packet used is TCP SYN packet with ISN(2361294848) and TOS(3). Upon receipt of this packet the access to SSH port is enabled for 60 seconds. SSH connection is allowed to the system for this duration window only. If remote system establises a connection using ssh within this duration, then the connection persists. Here, two methods to allow SPA are discussed. First one allows port opening for a particular IP address and second method uses the MAC address of requesting system to authenticate opening of port. The second method is useful when DHCP is configured to dynamically change IP address of requesting system.
PREREQUISITES
- System with mininet to simulate two hosts in a connected network. The net.py script given at https://foolsvilla.blogspot.com/2020/03/send-and-capture-icmp-packets-with-type.html may be used and executed using "sudo mn --custom net.py --topo mytopo" in linux to create two hosts h0(IP 10.0.0.1) and h1(10.0.0.2).
- Linux systems (I have used UBUNTU). Configuration of firewall rules is done using IPTABLES here.
- I have used xterm terminal emulator here. The default terminal may also be used. The hosts created using mininet are opened in different windows of terminal.
- Hping3 to craft packet and send. Any packet crafting tool may be used that allow the specific ISN and TOS field to be manipulated.
AUTHORIZATION USING IP ADDRESS
1) Open hosts 'h0' and 'h1' in xterm, from terminal$> xterm h0 h1
2) enable ssh in both hosts by running sshd service in xterm terminals of h0 and h1
$> /usr/sbin/sshd
3) check iptables rules in h1 to be default ACCEPT and login from 'h0' to 'h1' using ssh. Following on 'h0' xterm
$> ssh USERNAME@10.0.0.2
Here USERNAME is your username for SSH login. Allow authorization and login with 'h1' password.
4) Take backup of IPTABLES with
$> iptables-save > iptables_saved_rules_h1
This is restored after the simulation is complete.
5) setup drop all policy for incoming connection in 'h1' and allow established connection to continue.
# Set default chain policies
$> iptables -P INPUT DROP
$> iptables -P FORWARD DROP
$> iptables -P OUTPUT ACCEPT
# Accept on localhost
$> iptables -A INPUT -i lo -j ACCEPT
$> iptables -A OUTPUT -o lo -j ACCEPT
# Allow established sessions to receive traffic
$> iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
6) Now insertion of following rule will allow ssh connection from 'h0' to 'h1'
$> iptables -A INPUT -p tcp -s 10.0.0.1 --dport 22 -j ACCEPT
Deleting this rule will disallow any new connection, but the already established connection will continue
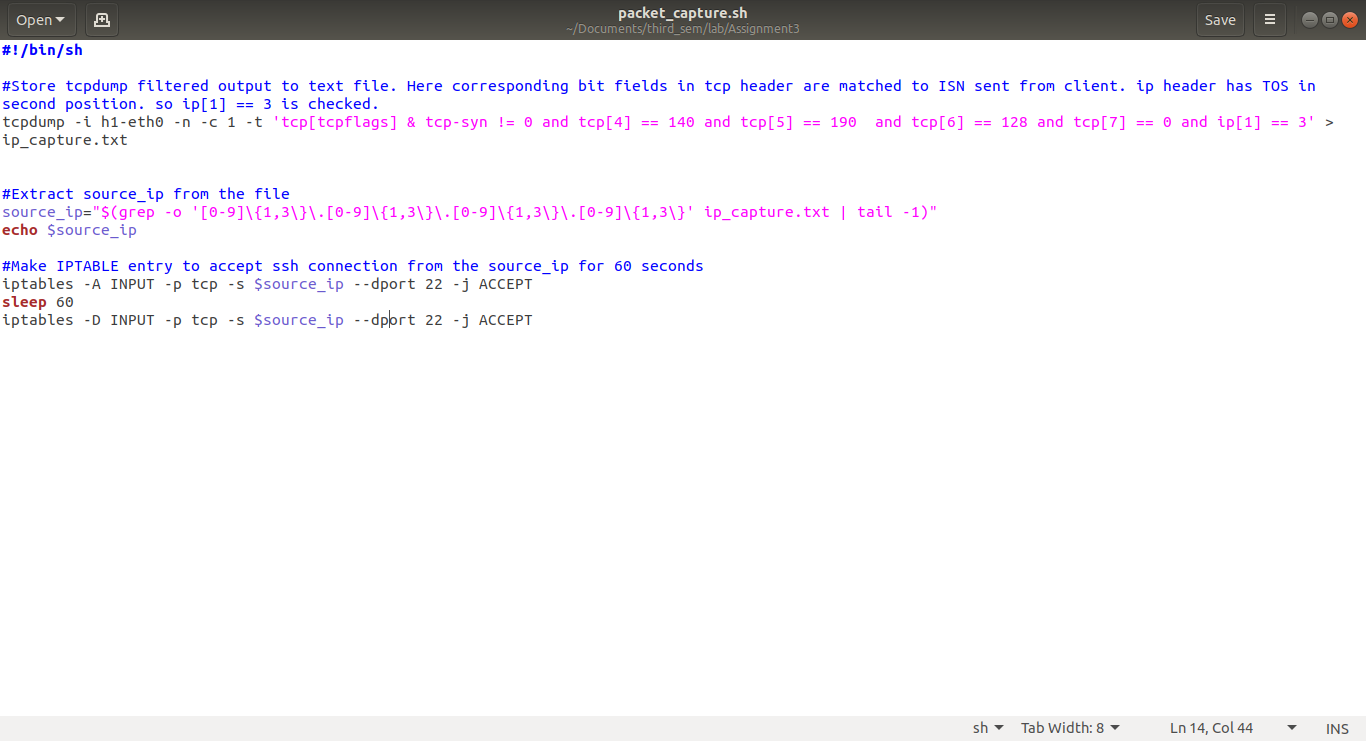
7) tcpdump listening on h1-eth0 interface is used to capture the SYN packet with specified sequence number and TOS. The script packet_capture.sh would take the tcpdump to text file and further extract IP from it using grep.
The IP is inserted into iptables for access on ssh port as mentioned above. The script further waits for 60 seconds and then deletes the entry from iptables. First make the script executable and then run it in 'h1'
$> chmod u+x packet_capture.sh
$> ./packet_capture.sh
8) One packet sent from client 'h0' to server 'h1' as follows:-
$> hping3 10.0.0.2 --setseq 2361294848 -p 22 -S -I h1-eth0 --tos 3 -c 1
9) ssh allowed for the matching IP for 60seconds and if connection is established during this time, the ssh session continues. If ssh login is not done within 60 seconds of reception of crafted packet, ssh not allowed.
1) ssh connection needs to be now established using MAC address. The script packet_capture_MAC.sh is used for this.
Here after extraction of ip address from authentication packet, ARP is done to obtain the MAC address. The ARP data is written into MAC_capture.txt and MAC_id extracted using grep. The MAC id is used to allow ssh through IPTABLE entry. Authentication duration is same as previous scenario.
$> iptables -A INPUT -p tcp -m mac --mac-source $MAC_id --dport 22 -j ACCEPT
2) The following packet sent from client 'h0' to server 'h1' authorizes the SSH port:-
$> hping3 10.0.0.2 --setseq 2361294848 -p 22 -S -I h1-eth0 --tos 3 -c 1


Comments
Post a Comment